* Copying P4D2 Fall 2017 into P4D2 2018 East. * Updated P4D2_2018_East VM. Added vagrant URL workaround, cdrom to VM. Updated to latest commits of BMV2, p4c, PI. Known issue with p4runtime exercise. * Applied patch from @antoninbas in and updated solution
Implementing Basic Tunneling
Introduction
In this exercise, we will add support for a basic tunneling protocol to the IP router that you completed in the previous assignment. To do so, we will define a new header type to encapsulate the IP packet and modify the switch to perform routing using our new header.
The new header type will contain a protocol ID, which indicates the type of packet being encapsulated, along with a destination ID to be used for routing.
Spoiler alert: There is a reference solution in the
solutionsub-directory. Feel free to compare your implementation to the reference.
Step 1: Run the (incomplete) starter code
The starter code for this assignment is in a file called basic_tunnel.p4
and is simply the solution to the IP router from the previous exercise.
Let's first compile this code to and send a packet between two end hosts to ensure that the IP routing is working as expected.
-
In your shell, run:
make runThis will:
- compile
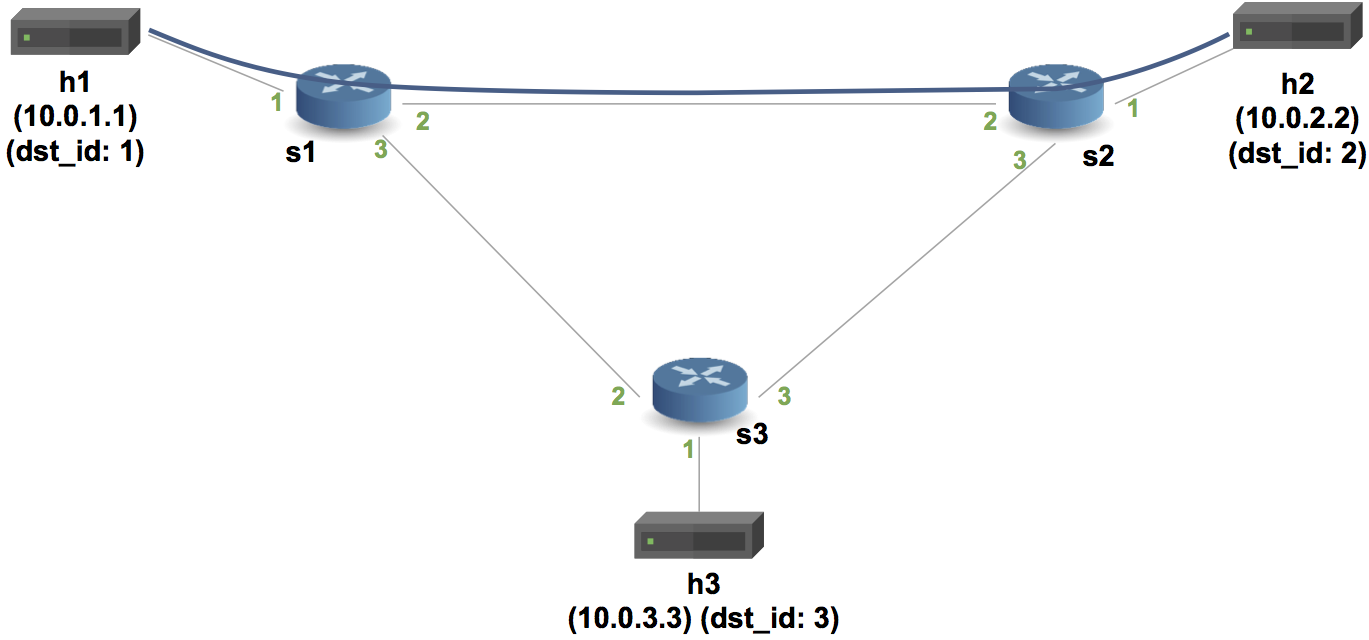
basic_tunnel.p4, and - start a Mininet instance with three switches (
s1,s2,s3) configured in a triangle, each connected to one host (h1,h2, andh3). - The hosts are assigned IPs of
10.0.1.1,10.0.2.2, and10.0.3.3.
- compile
-
You should now see a Mininet command prompt. Open two terminals for
h1andh2, respectively:mininet> xterm h1 h2 -
Each host includes a small Python-based messaging client and server. In
h2's xterm, start the server:./receive.py -
In
h1's xterm, send a message toh2:./send.py 10.0.2.2 "P4 is cool"The packet should be received at
h2. If you examine the received packet you should see that is consists of an Ethernet header, an IP header, a TCP header, and the message. If you change the destination IP address (e.g. try to send to10.0.3.3) then the message should not be received by h2. -
Type
exitorCtrl-Dto leave each xterm and the Mininet command line.
Each switch is forwarding based on the destination IP address. Your job is to change the switch functionality so that they instead decide the destination port using our new tunnel header.
A note about the control plane
A P4 program defines a packet-processing pipeline, but the rules within each table are inserted by the control plane. When a rule matches a packet, its action is invoked with parameters supplied by the control plane as part of the rule.
For this exercise, we have already added the necessary static control
plane entries. As part of bringing up the Mininet instance, the
make run command will install packet-processing rules in the tables
of each switch. These are defined in the sX-commands.txt files,
where X corresponds to the switch number.
Important: A P4 program also defines the interface between the
switch pipeline and control plane. The commands in the files
sX-commands.txt refer to specific tables, keys, and actions by name,
and any changes in the P4 program that add or rename tables, keys, or
actions will need to be reflected in these command files.
Step 2: Implement Basic Tunneling
The basic_tunnel.p4 file contains an implementation of a basic IP router.
It also contains comments marked with TODO which indicate the functionality
that you need to implement. A complete implementation of the basic_tunnel.p4
switch will be able to forward based on the contents of a custom encapsulation
header as well as perform normal IP forwarding if the encapsulation header
does not exist in the packet.
Your job will be to do the following:
- NOTE: A new header type has been added called
myTunnel_tthat contains two 16-bit fields:proto_idanddst_id. - NOTE: The
myTunnel_theader has been added to theheadersstruct. - TODO: Update the parser to extract either the
myTunnelheader oripv4header based on theetherTypefield in the Ethernet header. The etherType corresponding to the myTunnel header is0x1212. The parser should also extract theipv4header after themyTunnelheader ifproto_id==TYPE_IPV4(i.e. 0x0800). - TODO: Define a new action called
myTunnel_forwardthat simply sets the egress port (i.e.egress_specfield of thestandard_metadatabus) to the port number provided by the control plane. - TODO: Define a new table called
myTunnel_exactthat perfoms an exact match on thedst_idfield of themyTunnelheader. This table should invoke either themyTunnel_forwardaction if the there is a match in the table and it should invoke thedropaction otherwise. - TODO: Update the
applystatement in theMyIngresscontrol block to apply your newly definedmyTunnel_exacttable if themyTunnelheader is valid. Otherwise, invoke theipv4_lpmtable if theipv4header is valid. - TODO: Update the deparser to emit the
ethernet, thenmyTunnel, thenipv4headers. Remember that the deparser will only emit a header if it is valid. A header's implicit validity bit is set by the parser upon extraction. So there is no need to check header validity here. - TODO: Add static rules for your newly defined table so that the switches will forward correctly for each possible value of
dst_id. See the diagram below for the topology's port configuration as well as how we will assign IDs to hosts. For this step you will need to add your forwarding rules to thesX-commands.txtfiles.
Step 3: Run your solution
Follow the instructions from Step 1. This time when you send a packet from
h1 to h2 try using the following command to send a packet that uses
our new myTunnel header.
./send.py 10.0.2.2 "P4 is cool" --dst_id 2
You should see a packet arrive at h2 which contains the MyTunnel header.
Also note that changing the destination IP address will not prevent the packet
from arriving at h2. This is because the switch is no longer using the IP header for routing when the MyTunnel header is in the packet.
Python Scapy does not natively support the
myTunnelheader type so we have provided a file calledmyTunnel_header.pywhich adds support to Scapy for our new custom header. Feel free to inspect this file if you are interested in learning how to do this.
Food for thought
To make this tunneling exercise a bit more interesting (and realistic)
how might you change the P4 code to have the switches add the myTunnel
header to an IP packet upon ingress to the network and then remove the
myTunnel header as the packet leaves to the network to an end host?
Hints:
- The ingress switch will need to map the destination IP address to the corresponding
dst_idfor themyTunnelheader. Also remember to set explicitly set the validity bit for themyTunnelheader so that it can be emitted by the deparser. - The egress switch will need to remove the
myTunnelheader from the packet after looking up the appropriate output port using thedst_idfield.
Troubleshooting
There are several problems that might manifest as you develop your program:
-
basic_tunnel.p4might fail to compile. In this case,make runwill report the error emitted from the compiler and halt. -
basic_tunnel.p4might compile but fail to support the control plane rules in thes1-commands.txtthroughs3-command.txtfiles thatmake runtries to install using the Bmv2 CLI. In this case,make runwill log the CLI tool output in thelogsdirectory. Use these error messages to fix yourbasic_tunnel.p4implementation or forwarding rules. -
basic_tunnel.p4might compile, and the control plane rules might be installed, but the switch might not process packets in the desired way. The/tmp/p4s.<switch-name>.logfiles contain detailed logs that describing how each switch processes each packet. The output is detailed and can help pinpoint logic errors in your implementation.
Cleaning up Mininet
In the latter two cases above, make may leave a Mininet instance
running in the background. Use the following command to clean up
these instances:
make stop
Next Steps
Congratulations, your implementation works! Move onto the next assignment p4runtime!